Wanna Decryptor ransomware, commonly known as WannaCry or Wncry, is a malware that was responsible for most recent NHS cyber-attack. The NHS Digital confirmed that the NHS cyber-attack used WannaCry ransomware to infect all systems of over 16 UK trusts.
Several organizations from different parts of the world have suffered major cyber-attacks, and as a result, they have canceled their operations. WannaCry Ransomware is the new malware that has highly spread to most countries around the world.
What is Ransomware Malware?
Ransomware is a type of cyber-attack that involves hackers getting control of a computer system and blocking its access until the user has paid a ransom. For the cyber criminals to access a computer system, they must download a form of malicious software onto one device within the computer network. To achieve that, they have to incentivize the user to download or to click on the malware by mistake.
After downloading the malware onto the victim’s computer, the criminals are able to launch an effective attack that locks any file it finds on the network. However, the process is gradual and encrypts all files one after the other. The malware can lock your personal computer, smartphone or tablet and to unlock them, you will have to pay a ransom.
The first effective documented case came along in the year 2005 within the United States and started spreading around the world faster. The malware works in a very different way from that of others. The cyber criminals mostly add it to an email attachment, which masquerades as an innocent advertisement or attachment.
After opening, it immediately encrypts the hard drive and makes it impossible to retrieve or to access anything the hard drive contains – that might include photos, music or important documents. The criminals will demand varying ransoms. In the year 2014, victims in the UK had to pay $700 to access their files again. However, the criminals do not guarantee access to files after the ransom payment.
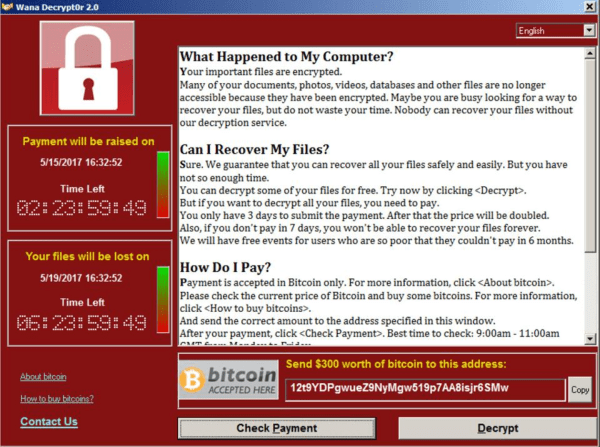
What is Wanna Decryptor
Travis Farral, Anomali’s director of security strategies, says that Wanna Decryptor is an encryption-based ransomware. The malware encrypts files using RSA and AES encryption ciphers and therefore the hackers can decrypt the system files directly using unique decryption keys.
Previously, victims of Wanna Decryptor received ransom notes containing instructions in the form of !Please Read Me!.txt files, and which linked to various ways of contacting the hacker. After infection, WannaCry changes the computer’s wallpapers with messages asking victims to start the decryptor download process on Dropbox. After that, they demand hundreds in cryptocurrency form for the download to start.
Put differently, after the Wanna Decryptor is inside the computer system, it makes encrypted copies of the particular file types and then deletes the originals thus leaving the victim with encrypted copies, which they can never access without the decryption key. The Wanna Decryptor also threatens data loss and heightens the ransom amount at a predetermined time, therefore, making a sense of urgency and highly increasing the chances of the victims paying the ransoms.
It is still unclear how WannaCry infected the computer systems but it can easily spread via phishing emails and after someone has visited a website featuring the malicious program. According to Avast, WanaCrypt0r 2.0 or Wanna Decryptor is possibly spreading on most computers by utilizing an Equation Group, an exploit group that people suspect of having ties with the NSA.
NSA Shadow Brokers
For many months, Shadow Brokers hacking group (a group that obtained files from NSA) started releasing hacking tools parts. In addition to the ransomware appearing in the UK, reportedly, it has appeared in Spain and many other countries around the globe. CCN-CERT, a Spanish organization that responds to computer emergencies has already issued an alert saying that it has already seen numerous ransomware attacks from WannaCry – the common version of Wanna Decryptor.
The ransomware infects machines by encrypting every file and circulates to other Windows machines on the network using command execution vulnerability through SMB. The vulnerability is associated with Microsoft machines and affects Windows Vista, 7, 8, 10 and Windows Server software versions. Microsoft announced the vulnerability earlier in March advising users to start patching their devices.
Microsoft managed to fix the MS17-010 in the March release. However, it is likely that the affected organizations had not patched their computer devices before the malware spread. The MS17-010, commonly known as the EternalBlue is linked to the Shadow brokers group.
How the Wanna Decryptor Spread?
The WannaCry is now advanced. While there are no confirmations made on the cause of infection, almost every attack has been through phishing emails. Worm-like fashions may also arise because the ransomware actors are now in the retooling stage. The attacks have confirmed that malware authors are always changing their tactics and responders have to be more vigilant to follow suit. Main cause of spread are clicking on the suspicious links or downloading suspicious documents from the mails. Those mails look legitimate and confused the user to made them to click on the malware.
How effective is an Antivirus software against Ransomware attack
Computer antivirus software can work to protect your machine but cyber criminals always work on newer ways to override the protection. They trick the users to get the permission to enter into the system. So Antivirus are not the full proof protection for this type of crypto malware or Ransomware. Use the multiple layer of protection to keep your computer safe from cyber attacks.
Larger companies with advanced security systems can manage to spot the malware and isolate documents to reduce damages. However, individuals are not lucky enough and can lose access to their information at the end. In fact, cyber criminals demand payments in return for files unlock. The payments are mostly in the form of online crypto currency such as Bitcoin.
How to protect your computer from WannaCry or Any ransomware
Ramsonware is a multi-million dollar crime process that is targeting everyone including police departments, hospitals, insurance companies and online casinos. Due to its high profitability nature, most traditional cyber thieves are now abandoning their old money making methods – stealing bank account credentials and credit card numbers – to invest in the ransomware scheme.
Do not expect lawmakers to help you fight ransomware attacks. That way, you will end up paying many ransoms, as most victims have done. In 2016 alone, Americans lost over $24 million to cyber-criminals. Including if you have backed up your data in the safe places, the attack may still cost you. For example, CrytoWall ransomware victims have suffered around $325 million in damages since ransomware strain came into existence. They incurred machines disinfection costs and backup data restoration, which took days or weeks. The cost will highly depend on the organization.
If you are at a higher risk of ransomware attacks, you can take several steps to protect your business and yourself. The following are a few things to do.
Back up your data regularly
The most effective defense against ransomware malware is to outwit cyber criminals by reducing your vulnerability to their threats. In other words, you should regularly back up your data – on a daily basis when possible – to avoid paying the ransoms including after they have locked the servers and computers. Companies have lost thousands of files in a single attack. With backup, you can always retrieve your data.
Best Free Backup Tools for PC to backup offline
Most ransomware programs are known to search out the backup systems to cipher and lock, too. After they have gained entry into a computer, they will manually work their way through the network to access the servers. Therefore, if you have opted for local storage devices or server instead of the cloud, they should be offline and you should not connect them directly to your desktop systems where the attacker or the ransomware can easily reach them.
If you are among the people who store their data in network shares, you should know that it is at a high risk just like the desktop system. Individuals who do their backup offline are safe, if the data is unreachable from the infected machine. That is also true for people who use external hard drives to do their machine backups. Connect the drives when doing a backup and then disconnect it. If your backup is connected at the particular time the malware runs, it might also be encrypted. Data backups will not make the attack painless because your business operations might stop for days or even weeks. Hospitals have paid the ransom amounts to save lives.
Avoid clicking on any suspicious email
The main method of infecting computer systems involves hacker’s favorite bait – spray-n-pray phishing attack. The attack involves spamming users with emails that feature malicious attachments. The emails may also instruct users to click on URLs to allow the malware to crawl surreptitiously into the machine. Due to ransomware attacks increase, most organizations have temporarily blocked Yahoo email accounts access – they are apparently the accounts which attackers phish.
What is ransomware? & tips to prevent it
Ransomware attackers have also adapted another effective method, malvertising, which involves compromising advertisers’ networks by embedding the malware into an advert that they deliver through the popular and most trusted websites.You can use ad blockers to block the malicious ads. Patch any known browser security hole to thwart malvertising.
Patch and block
As a user, you are not the stopgap for infections. You are more likely to open an attachment, visit an infected website and whenever that happens, you need protection form the security technology. Many available systems use deeper learning to detect malware like ransomware and block them. However, security products are fallible. Otherwise, businesses and individuals would not be a target of many ransomware and other malware.
Companies should apply other standardized security measures to protect their data. The methods include patching software program security holes to prevent exploitation from malicious systems and infections on their systems. In web attacks, they are exploiting vulnerabilities in the third-party plugins (Java and Flash) and updating them regularly is helpful.
Another option is to use whistling software because the lists will not allow installation of unapproved software. The administrator will first scan the machine to check the legitimate software programs running on the machine and then configure them to prevent executable files from installation or running.
System administrators can also use other methods including limiting system’s security permission – to prevent any malware from installing on a system with the administrator’s permission. Administrators can also employ segmentation access to prevent critical data access with redundant servers.
Instead of allowing hundreds of employees to access data on one server, administrators can divide employees into small groups so that if a ransomware locks one server, chances of affecting the others will be lower. The tactic can also force attackers to situate and lock down the other servers to make an assault effective.
Disconnect if you have an infection
MedStar Health administrators were able to shut down the organization’s network operations to stop the infection from spreading. Administrators should disconnect the infected systems from the network and disable Bluetooth and WiFi on machines – to prevent the spread of the malware through these methods.
After that, the victim should try to determine the type of ransomware malware that affected them. If it is among the known variants, most antivirus companies such as Kaspersky Lab have the decryptors that can help bypass the lock or unlock the files without having to pay the ransom – that will depend on the attacker’s encryption method quality.
If you have not backed up your files and you cannot find the method to access the files, pay the ransom amount (it is the only option). In the traditional hacks, the level of pain is low and victims are able to move on. However, ransomware can bring your business’s operation to a standstill. In case of individuals, accessing family photos and the other personal files becomes impossible after an infection. The level of pain associated with that is high. We can stop fueling the engine that is driving the ransomware attacks by not paying. However, that depends on the expected loss.
Companies and organizations that highly depend on daily data access – particularly those that cannot afford to lose data access – should be more worried about ransomware. That means hospitals, banks, police departments, Congress, airport, and airlines should remain vigilant. Large corporations and government agencies are also at a threat. The other attack is home computers.
How to remove WannaCry ransomware and recover data
There is no effective method is available till now to decrypt and recover the infected files back. However removal of the infection (without recovering data) is possible by scanning with malware scanners. But we do not recommend to do anything if your data is important as it can lead to permanent lost of your data. We will update you as soon as we get any update regarding WannaCry Ransomware.
Below is a common practice to give it a try to recover the files from a ransomware virus attack.
Before starting process of removing WannaCry from computer, read the below instructions carefully.
So you have planned NOT to Pay ransom and want to give it a try to restore your files. But before starting removal process you have to keep in mind that in this removal process you can loose your data / files completely forever.
Please dare to start removal process at your own risk as you can loose your data or any of your important document permanently. After this you can even loose your chance to pay ransom to recover data.
Steps to remove Ransomware and try to recover .WNCRY infected files
Steps to remove WannaCry cryptolocker Virus from computer.
- Download and scan your computer with Hitman Pro and Malwarebytes anti malware software to clean up any trojan, malware from your computer to stop downloading WannaCry related malware again on your computer.
- Scan with a Good Antivirus software or with any second opinion scanner.
- By doing these above steps chances are that WannaCry infection has get removed, But you can not decrypt the encrypted files. In further steps we will try to recover the files.
- Try to recover files with the System Restore.
- If you are still unable to recover, then the last method you can try is using File Recovery Software like Recuva. You can also use other useful Data Recovery Software.
Why cyber police is unable to catch these bastards. What the hell is this BitCoin? Why government is not banning Bitcoin? Bitcoin is the root cause of illegal activities all over the world.
Is there any way to decrypt the .WNCRY encrypted files? Can changing the extension will work or not?
Actually No. Renaming the file will not work. The only option that you can give a try is to recover the old copy of the files by using data recovery software. Anyway I have already added the steps in the article which can be followed for any standard ransomware attacked to recover the files. Though WNCRY is also deletes the shadow copy of the deleted files. But still are are some options that you can try. But still chances are very very less.
WannaCry ransomware is responsible for the biggest cyber attack of the history. Thank you for the tips for its protection. Though users who have already using a paid antivirus software are immune to this attack as all antivirus companies patched their software to detect this threat. Even Microsoft have also released a patch for the Windows.
Yes it is right. Visit to patch Windows. https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/