Ransomware Victims are increasing very fast this year after appearance of the new Locky Ransomware Virus. Locky is the biggest threat of the 2016 so far. It was first detected in February, 2016. Creator of this ransom virus are spreading it very aggressively all over the world through spam emails and compromised websites. All of the Top security companies like Norton, Sophos, McAfee declared that they are seeing aggressive behavior of this Locky Ranosmware. We have tried to gather all possible information that you need to know about this threat.
The Below graph by Norton is showing that how fast it is spreading after detection of locky Ransomware. Victims rise all of sudden in Feb and March and continue going up after appearance of it .
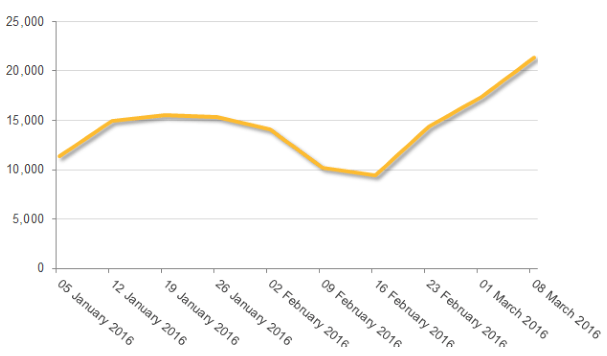
Source: Symantec.com
What is Locky Ransomware Virus and what it does
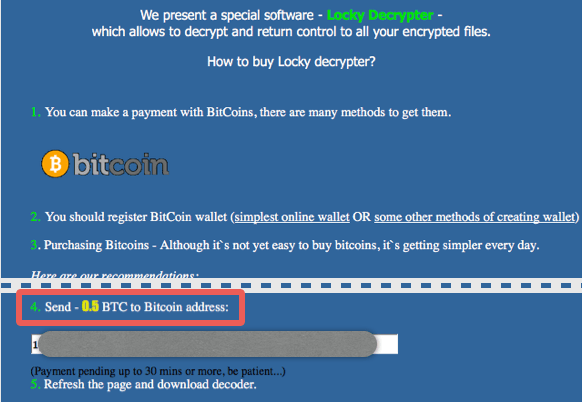
Locky encrypts file on the victim’s computer and changed their extension to the .locky. Then they ask for 0.5 Bitcoin to 1 Bitcoin (Approx $200 to $400) as ransom to decrypt the files. There is no other option then either give them ransom or loose data if you have no back up of the data. It is not just encrypting your C drive but all the drives even attached USB drives or external drives. It also attacks on all the computers in the network regardless of running any OS Linux or Os X or Windows and encrypt their files as well. So it is a bigger threat to all business users and they need special precaution to keep away from this Malware.
How is Locky Virus spreading
Locky is pushing malware very aggressively through mails and compromised websites. They are spreading it with Spam email campaigns with the subjects like:
“ATTN: Invoice – [RANDOM NUMBERS]” ,
“Tracking Documents”,
“Scanned Image”
And many more…
At first receiver will think that it is a legitimate mail and as he try to download the attachment this malware start to download the cryptoware Rocky.
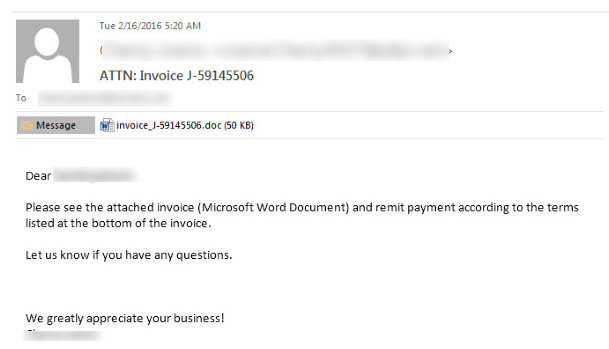
These malware or email campaign can be detected easily as they have not any fixed pattern. They keep changing their strategy frequently, that they can not get detected easily. Mostly sender appeared as land[RANDOM NUMBER]@VICTIM DOMAIN.com etc in these fake emails.
According to Symantec they have blocked more then 5 Million spam emails associated with locky campaign in 2 days.
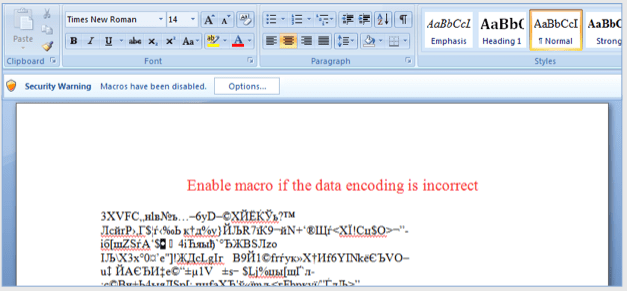
These emails contains a Word file with a malicious macro. As you try to open the document it ask permission to run, and as user allow it, he become the victim of Locky Ransomware.
Recently McAfee revealed that now Locky is using the Javascript file as trojan which download the Locky Ransomware if get executed any how. In its initial stage it is spreading widely in US, France and Japan countries.
How do I detect if my computer is infected with Locky?
Though after getting infected you don’t need to ask this question as Locky itself will tell you that you are a victim and change the desktop background some thing like this for the further steps to pay ransom amount.
It Display a message like this
“!!! Important information !!!! All of your files are encrypted with RSA-2048 and AES-128 ciphers. Decrypting of your files is only possible with the private key and decrypt program, which is on our secret server.”
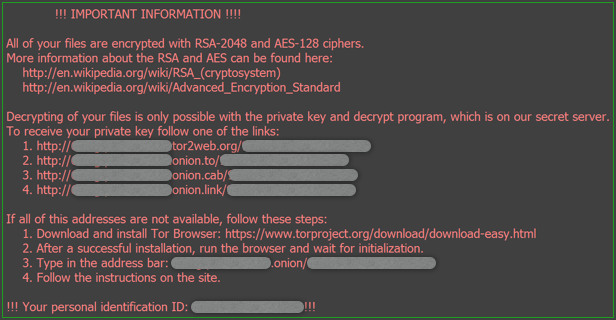
Source: Sophos.com
You will find mostly all of your files changed to an extension .locky with encrypted format. Encrypted means they are no use of you and to make them usable again you need to pay ransom to get the decryption key.
Is it possible to recover / decrypt files encrypted by Locky
If it is about decryption the straight answer is No. You can not decrypt these encrypted file without the key in any manner. However if it is about recovery then their are slight chances that if you can recover them from the system shadow or with System restore. Though the chances are very less with system restore, but you can give it a try. If you are wise enough and have already taken offline backup of your important that is great because it is the only method to recover your files, but for this you have take steps in advance. After become victim the only option is to pay Ransom.
Will I pay ransom? Is it safe?
If your files are really very important and you have backup of them then of course you have no other option. But we don’t have to pay them as it only encourage them to it again and again. Even when you are paying money using any of your method there is risk that they can even steal your financial information as well.
If your files are not important and you decided not to give ransom now the next step is to how do you remove and get rid of this problem from your computer.
How to Remove Locky Ransomware from computer
Before starting process of how to remove locky from computer, read the below instructions carefully.
So you have planned NOT to Pay ransom and want to restore your files. But before starting removal process you have to keep in mind that in this removal process you can loose your data / files completely forever.
Please dare to start removal process at your own risk as you can loose your data or any of your important document permanently.
Steps to remove Locky Ransomware and try to recover files
Steps to remove Locky ransomware Virus from computer.
- Download and scan your computer with Hitman Pro and Malwarebytes anti malware software to clean up any trojan, malware from your computer to stop downloading Locky again on your computer.
- Scan with a Good Antivirus software or with any second opinion scanner.
- By doing these above steps chances are that locky infection has get removed, but you can not decrypt the encrypted files. In further steps we will try to recover the files.
- Download ShadowExplorer. Install it and try to restore files with this software.
- If you are unable to recover with the step 4 try to recover files with the System Restore.
- If you are still unable to recover, then the last method you can try is using File Recovery Software like Recuva. You can also use other useful software like EaseUS data Recovery Wizard, R-Studio etc.
Locky related file location and registry entries.
Files related to locky
%UserpProfile%\Desktop\_Locky_recover_instructions.bmp %UserpProfile%\Desktop\_Locky_recover_instructions.txt %Temp%\[random].exe
Registry Entries of Locky
HKCU\Software\Locky HKCU\Software\Locky\id HKCU\Software\Locky\pubkey HKCU\Software\Locky\paytext HKCU\Software\Locky\completed 1 HKCU\Control Panel\Desktop\Wallpaper "%UserProfile%\Desktop\_Locky_recover_instructions.bmp"
How to prevent locky entering into the system
As the saying prevention is better then cure. Same is in this case. Always be prepared to prevent these threats to infect the computer. See some below tips for the protection of any ransomware or any threat. Read the tips below for how to avoid locky virus infection in your computer.
- Backup your important files regularly to an offline location Even if you are using an online cloud backup.
- Keep your security software updated to catch the every possible variant of the malware trojan or ransomware.
- Keep your OS updated.
- Do not open email attachment if they are not from trusted source. Always look the sender email address for the authenticity of the email. Spam emails is the largest method to spread ransomware.
- If computer ask for any permission always be careful, If you have not really installing something, Don’t click blindly on Allow button.
- Install Microsoft Office Viewer to view the document files as this software have no option to run macros. Running Macros are greater risk which lead to activate malware / ransomware on the computer.
- Use a good Antivirus Software having an Anti-Ransomware feature and keep that updated regularly.
Anti-Ransomware Tools to Avoid Locky Virus
Right now we only found below two Ransom Virus Protection software which are effective in preventing Ransoware family of CTB-Locker, Locky and TeslaCrypt like Cryptoware. You can use the below tools as preventive Vaccination for Locky Virus.
For more tools go to Best AntiRansomware Software.
Hopefully above guide will help you if you have any other suggestion or information regarding Locky Virus then please share here to help others.
Useful information, thanks for this great update. Bitdefender is a great tool and does not impact system any how. I think everyone should have to install that free utility.